What is eBPF?
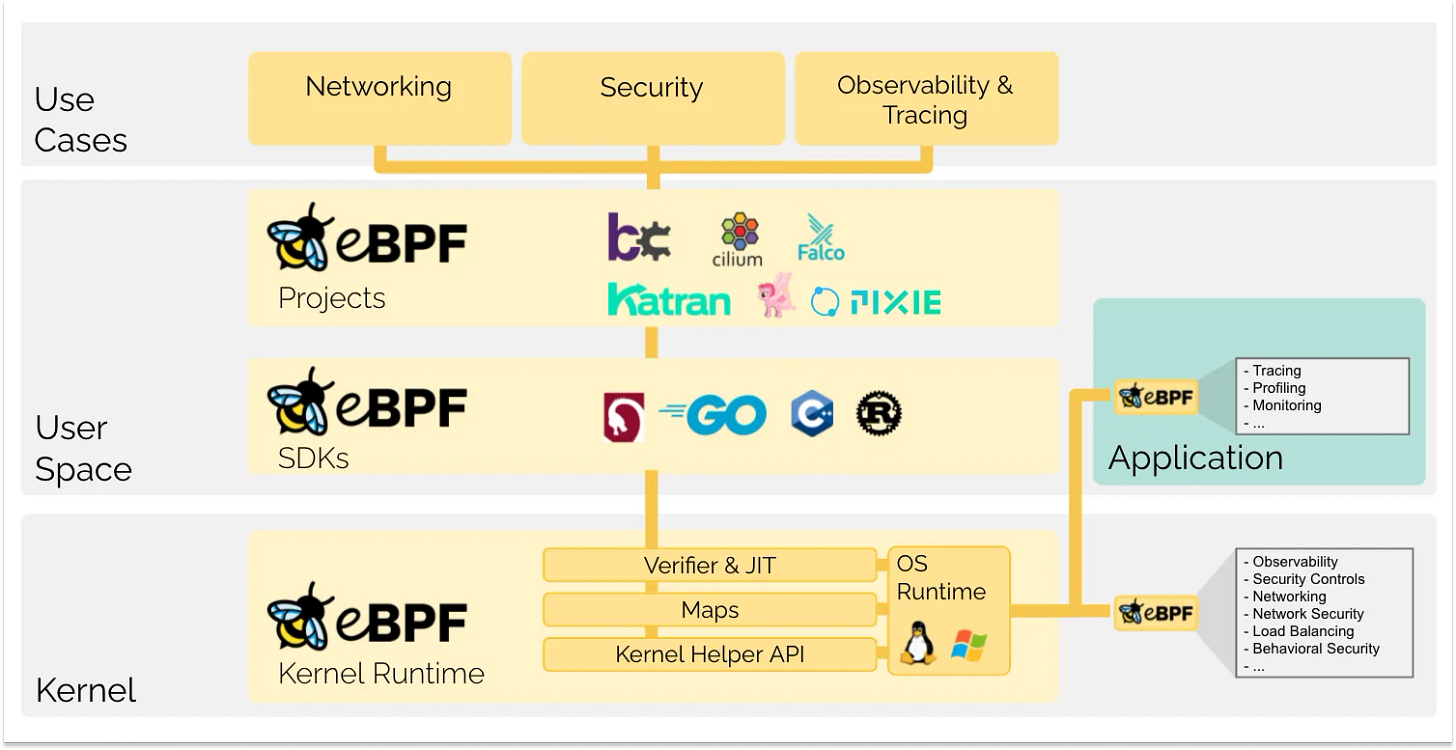
eBPF (extended Berkeley Packet Filter) is an in-kernel “virtual machine” that lets you run programs in the Linux kernel—powering tracing, networking, and security without kernel recompiles.
🔗 Useful Links
“What is eBPF?” on eBPF.io
High-level overview of the eBPF “VM”, its use cases, and ecosystem.
Linux kernel BPF documentation
Definitive in-kernel reference for helpers, program types, verifier rules, maps.
🗺️ eBPFChirp Learning Path
Pick Your Toolchain
How to choose the right eBPF language (C, Rust, Go), and library (libbpf, cilium/ebpf, Aya…), before you start hacking.
Build Your First Program: eBPF Process Monitor
Step-by-step tutorial that captures execve system calls, and streams observed event data to user space—your “Hello, world” for eBPF.
Observability Advanced Use Cases
Real-Time Encrypted Traffic Observability — Monitor SSL/TLS flows in real time without touching a line of application code.
PostgreSQL Traffic Observability — tap into PostgreSQL read/write system calls to stream and classify queries in real time.
Redis Traffic Observability — tap into Redis read/write system calls to parse RESP commands and flag anomalous patterns in real time.
Networking Advanced Use Cases
Beyond “1 Port <=> 1 Socket” – eBPF’s
sk_lookuphook breaks the “one-socket, one-port” rule by letting the kernel reroute new connections to any socket you choose.
Transparent Proxying – service-mesh-style traffic steering with zero sidecars.
Accelerate Local Socket Communication — SOCKMAP eBPF splices local TCP sockets in-kernel, reducing loopback latency up to 30%.
Security Advanced Use Cases
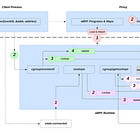
eBPF and Linux Security Modules — Lock down Kubernetes workloads with LSM-BPF policies that trace, detect, and block runtime threats.
Other Advanced eBPF Topics
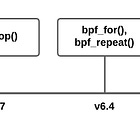
Modern eBPF gives you verified-safe loops and iterators—
#pragma unroll, bounded loops,bpf_loop(), and object/map iterators.
Tracepoints are stable but limited, kprobes can latch onto any kernel symbol with a bit more overhead, while fprobes (fentry/fexit) give the fastest inline hooks—pick the one whose trade-off of coverage vs performance best fits your tracing job.
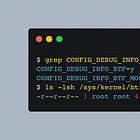
BTF is compact kernel-type metadata that enables CO-RE (Compile-Once, Run-Everywhere).
Easily observe all the eBPF Maps on the system using eBPF Iterators features.
Happy tracing, and keep 🐝‑ing!





![What Insights Can eBPF Provide into Real-Time SSL/TLS Encrypted Traffic and How? [Sponsored]](https://substackcdn.com/image/fetch/$s_!Jkmf!,w_140,h_140,c_fill,f_auto,q_auto:good,fl_progressive:steep,g_auto/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fa520d4b0-98b9-4b3e-92af-c5fc28c84081_2000x1354.png)

![Can eBPF Detect Anomalous Redis Message Patterns Before They Become Problems? [Sponsored]](https://substackcdn.com/image/fetch/$s_!3Uf9!,w_140,h_140,c_fill,f_auto,q_auto:good,fl_progressive:steep,g_auto/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F34eadfbb-9bd1-4fc6-8d90-356ca359b351_2974x3538.heic)


![Securing Kubernetes Workloads using LSM-BPF [Sponsored]](https://substackcdn.com/image/fetch/$s_!JiCw!,w_140,h_140,c_fill,f_auto,q_auto:good,fl_progressive:steep,g_auto/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F2123377a-8024-4ada-be13-3d4cc4bd2d58_4140x1463.png)